How to configure Single Sign on using Azure Active Directory (SAML2.0)
How to configure single sign-on using Azure AD (SAML2.0)

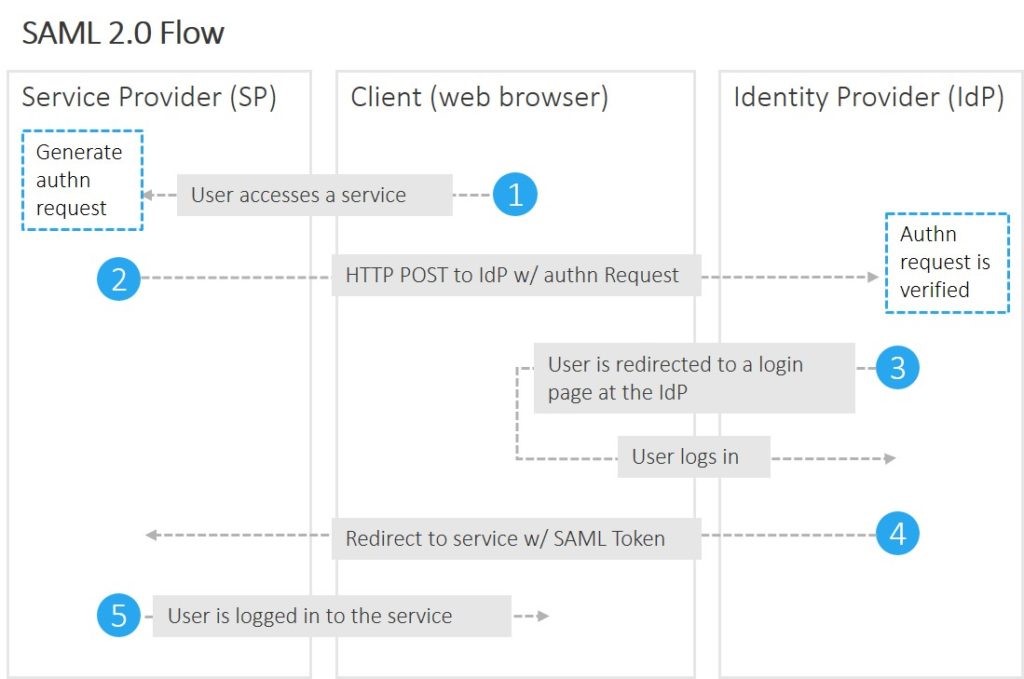
This guide will walk you through a standard SSO integration with Azure Active Directory as the Identity Provider (IdP) and ITM Platform as the Service Provider (Sdp). Before proceeding, we advise you to get familiar with the Single Sign-On process in ITM Platform.
Azure configuration
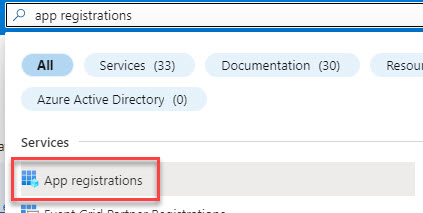
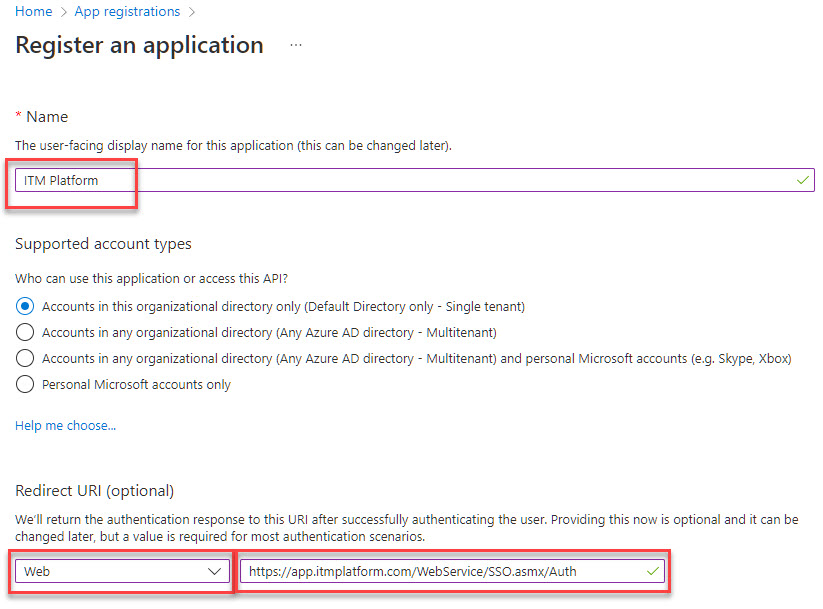
In your Azure portal, search for App Registrations and click on Create new app registration, or edit an existing one
Input a Name, and choose Web as the redirect URL, adding https://app.itmplatform.com/WebService/SSO.asmx/Auth
At this point, your application is generated. Now, Generate an Application ID URI by clicking on Add an Application ID: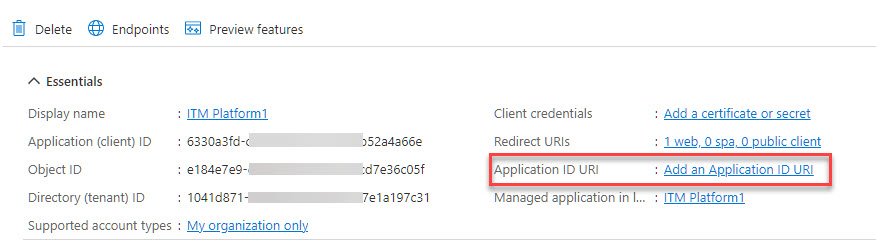
Click on set.
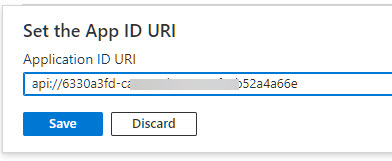
Accept the suggested URI or set your own, and save:
Click on Redirect URIs
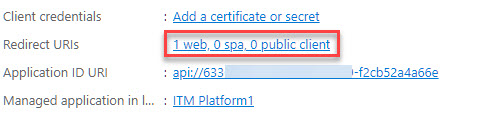
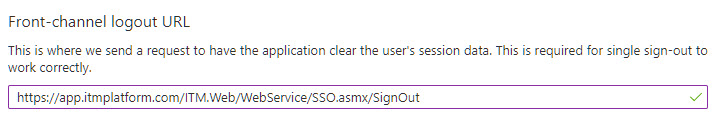
Add https://app.itmplatform.com/ITM.Web/WebService/SSO.asmx/SignOut to the front-channel logout URL and save
Copy the previously generated Application ID URI, and the SAML-P sign-on endpoint and SAML-P sign-out endpoint. To access all your endpoints, click on the Endpoints button of your registered app.
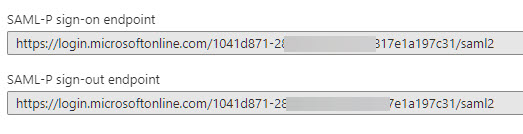
By now, you should have
- Application ID URI
- SAML-P sign-out endpoint
- SAML-P sign-out endpoint
ITM Platform configuration
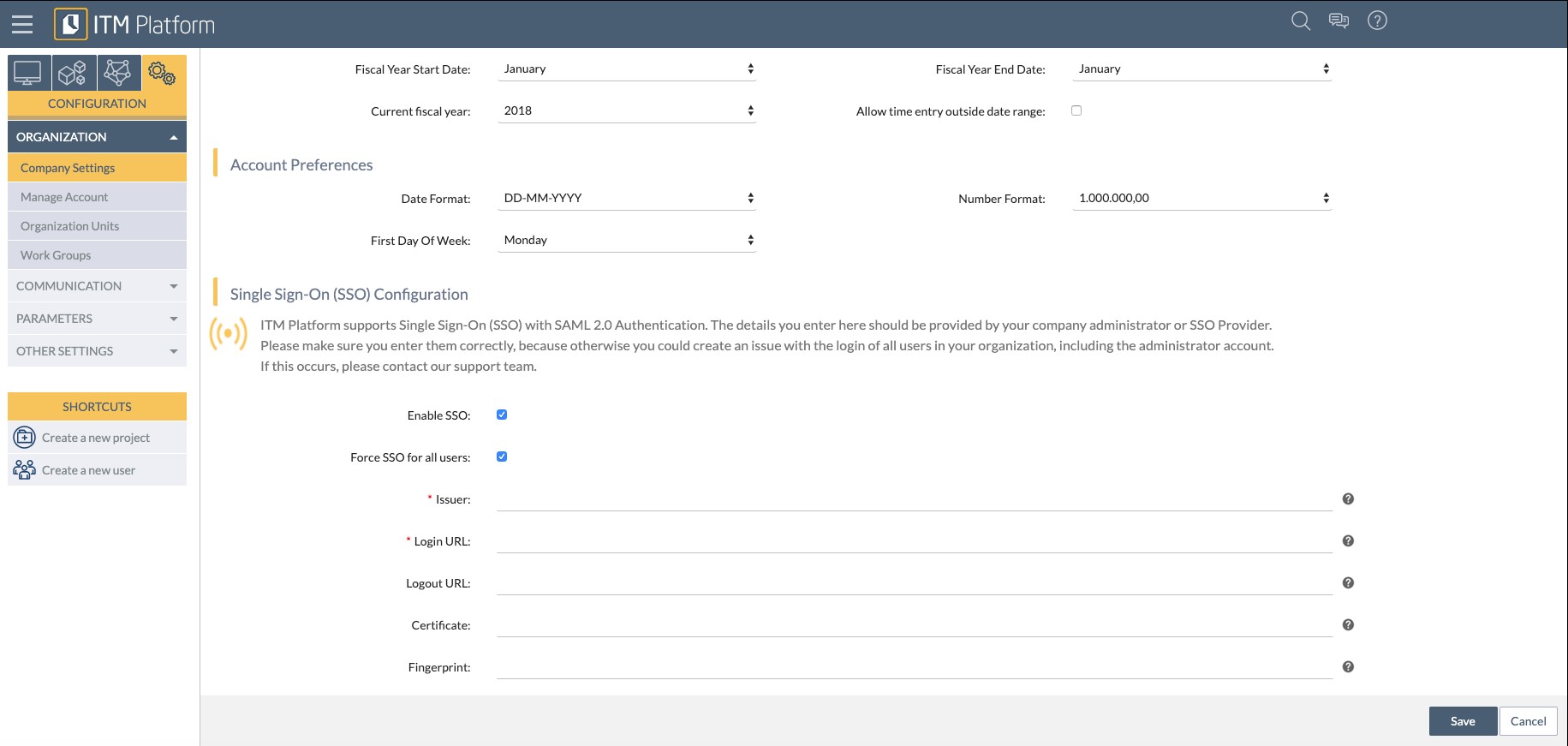
On the left menu, go to CONFIGURATION > ORGANIZATION > Company Settings. Scroll down to “Single Sign-On (SSO) Configuration”
- Tick “Enable SSO”
- We don’t recommend ticking “Force SSO for all users” until you have tested all works fine. Otherwise, you may be locked out. If this happens, please get in touch with support@itmplatform.com
- Issuer: paste the “Application ID URI” provided by Azure
- Login URL: paste the “SAML-P sign-on endpoint” provided by Azure
- Logout URL: paste the “SAML-P sign-on endpoint” provided by Azure
- If you generated a certificate in Azure, paste it in the Certificate field, as well as the SHA-256 fingerprint.
- Save
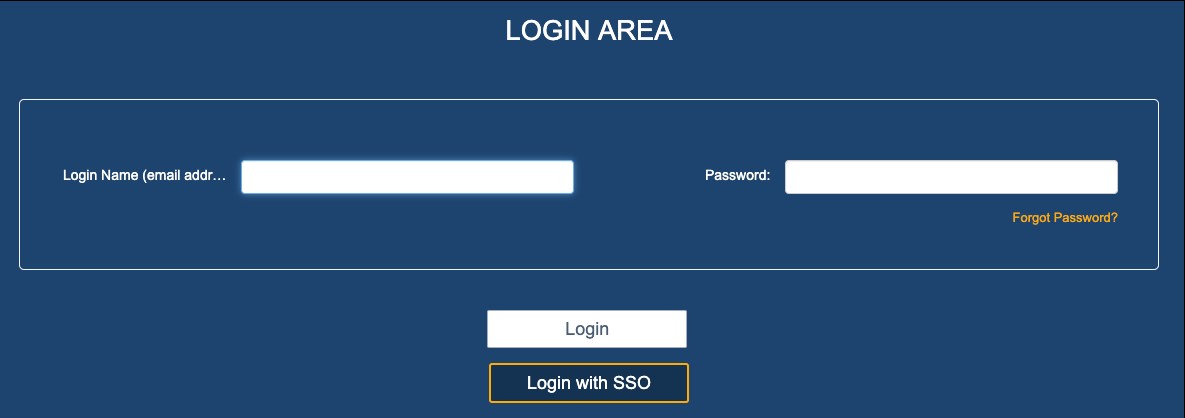
To test it, log out and when prompted on the login page, click on “Login with SSO.” You should be redirected to Azure’s login page and fill out your credentials (we recommend you select “remember me” ). You will then be redirected to ITM Platform’s home page, and from then on, clicking on “Login with SSO” will lead you to ITM Platform’s home page.